Post-Quantum Encryption and the Domain Ecosystem: Preparing for the Next Era

The internet is built on a foundation of cryptographic trust. Every time you visit a website, send an email, or resolve a domain name, complex protocols perform silent verifications to ensure you connect to the legitimate server. For decades, algorithms like RSA and Elliptic Curve Cryptography (ECC) have been the custodians of this digital realm.
However, a seismic shift is coming. We are approaching the edge of the Post-Quantum Era—a time when quantum computers will possess the processing power to shatter the cryptographic shields protecting the global internet.
For the domain ecosystem—registries, registrars, and the Domain Name System (DNS) itself—this isn’t just a technical upgrade; it is an existential necessity. Adopting Post-Quantum Cryptography (PQC) is the only way to preserve the integrity of our digital identities.

The "Q-Day" Threat: Why It Matters Now
You might be thinking, “Quantum computers capable of breaking encryption are years away. Why worry now?”
Security experts refer to the day quantum computers break current encryption as “Q-Day.” While Q-Day might be a decade away, the threat is immediate due to a strategy employed by malicious actors known as “Harvest Now, Decrypt Later” (HNDL). Hackers and state-sponsored entities are currently scraping and storing vast amounts of encrypted traffic. They are holding this data, waiting for the day a quantum computer can unlock it.
If your domain infrastructure, internal communications, or customer data is encrypted with today’s standards, it is already vulnerable to tomorrow’s machines.

Vulnerability Point 1: The Breakdown of SSL/TLS
The most visible impact of the quantum threat is on SSL/TLS certificates, the technology that gives us the padlock icon and “HTTPS” in the browser bar.
Current certificates use public-key cryptography (usually RSA or ECC) to establish a secure connection. A sufficiently powerful quantum computer running Shor’s Algorithm could derive the private key from the public key in minutes.
- The Consequence: Attackers could impersonate your website perfectly. They could intercept sensitive user data (passwords, credit cards) without the user or the browser ever detecting a problem.
- The Fix: We must transition to PQC algorithms selected by NIST (like CRYSTALS-Kyber). This will likely involve Hybrid Certificates initially, certificates that contain both a traditional key (for compatibility) and a quantum-safe key (for future-proofing).
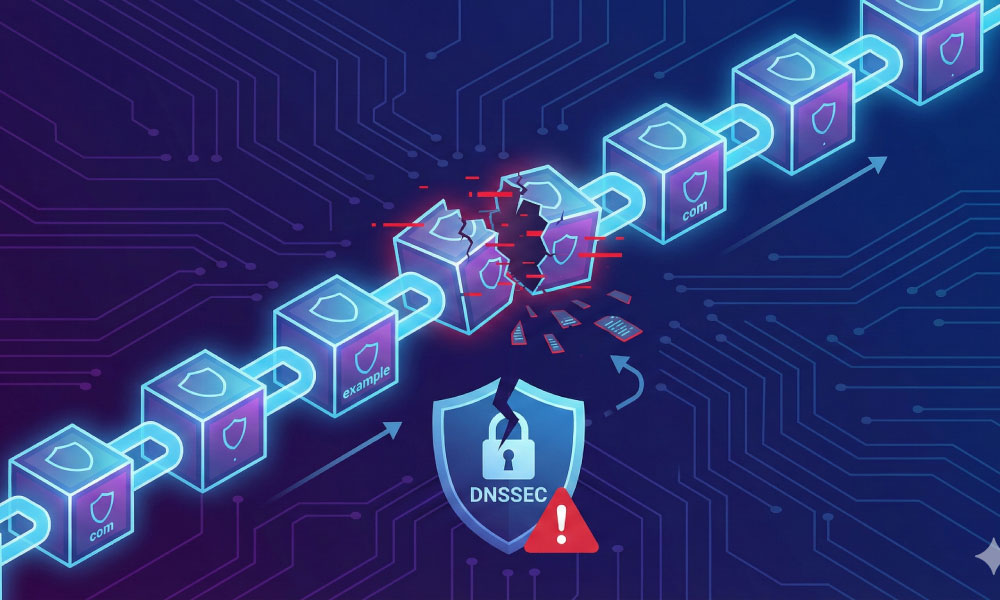
Vulnerability Point 2: DNSSEC and the Chain of Trust
While SSL secures the connection after you find the website, the Domain Name System Security Extensions (DNSSEC) ensures you find the right website in the first place. DNSSEC adds a layer of trust to the internet’s phonebook by digitally signing DNS records.
Currently, DNSSEC relies heavily on RSA and ECDSA signatures.
- The Consequence: If a quantum computer breaks these signature algorithms, attackers could forge DNS responses. They could redirect traffic from yourbank.com to a malicious clone server. Because the forged signature would mathematically “pass” validation, even strict security resolvers would be fooled.
- The Challenge: Updating DNSSEC for the post-quantum era is harder than updating SSL. PQC signatures (like FALCON or SPHINCS+) are significantly larger in file size. Stuffing these large signatures into DNS packets could cause fragmentation and packet loss, potentially breaking the internet’s resolution speed. The engineering community is currently racing to optimize these algorithms for the DNS environment.
The Role of Registries and Registrars
The domain ecosystem is a supply chain. If the Registry (the operator of TLDs like .com or .ai) or the Registrar (where you buy the domain) is compromised, the downstream user is vulnerable.
Extensible Provisioning Protocol (EPP) is the language registrars use to talk to registries. This communication pipeline handles domain transfers, updates, and ownership changes. It must be secured by quantum-resistant TLS tunnels to prevent unauthorized domain hijackings in the future.
Domain industry leaders must begin implementing Crypto-Agility. This refers to the ability to easily swap out cryptographic algorithms without rewriting the entire infrastructure. If a specific PQC algorithm is found to be flawed in the future, agile systems can switch to a new one instantly.

How to Prepare: A Checklist for Domain Owners
You don’t need to be a cryptographer to prepare your digital assets for the quantum shift. Here is a strategic roadmap:
- Inventory Your Cryptography: You cannot protect what you don’t know you have. Use automated tools to scan your network for all digital certificates and identify which algorithms they use.
- Prioritize High-Value Data: Identify data that has a long shelf life (e.g., healthcare records, government secrets, intellectual property). Apply quantum-safe protections to these assets first to counter HNDL attacks.
- Talk to Your Vendors: Ask your Certificate Authority (CA) and your DNS provider about their PQC roadmap. Are they testing hybrid certificates? When do they plan to support PQC-enabled DNSSEC?
- Embrace Automation: The days of manually renewing certificates are over. PQC certificates may have shorter lifespans and higher complexity. Implement Automated Certificate Management Environments (ACME) to handle renewals and re-keying instantly.

The New Digital Handshake
The domain name is more than just a web address; it is the anchor of your digital brand. For the last 30 years, we have trusted specific mathematical locks to secure that anchor. As we move into the quantum era, those locks must serve a new purpose.
The transition to Post-Quantum Cryptography is not just a patch; it is a rebuilding of the internet’s trust layer. By preparing now, domain owners ensure that their “digital handshake” remains firm, secure, and trusted, no matter how powerful the computers of the future become.
