DigiCert TLS Certificates Move to 199-Day Validity

DigiCert has officially announced that public TLS/SSL certificates will move to a maximum validity period of 199 days, effective 24 February 2026. This update applies to all public TLS certificates, including Domain Validation (DV), Organization Validation (OV), and Extended Validation (EV) certificates.
This change is part of a broader, long-term industry initiative led by browser vendors and certificate authorities to strengthen the security and trust of the public internet. For enterprises, the shift introduces important considerations around certificate lifecycle planning, operational readiness, and risk management.
This article explains the background of the change, what it means for enterprise environments, and how organizations can prepare.
Maximum validity period of public TLS/SSL
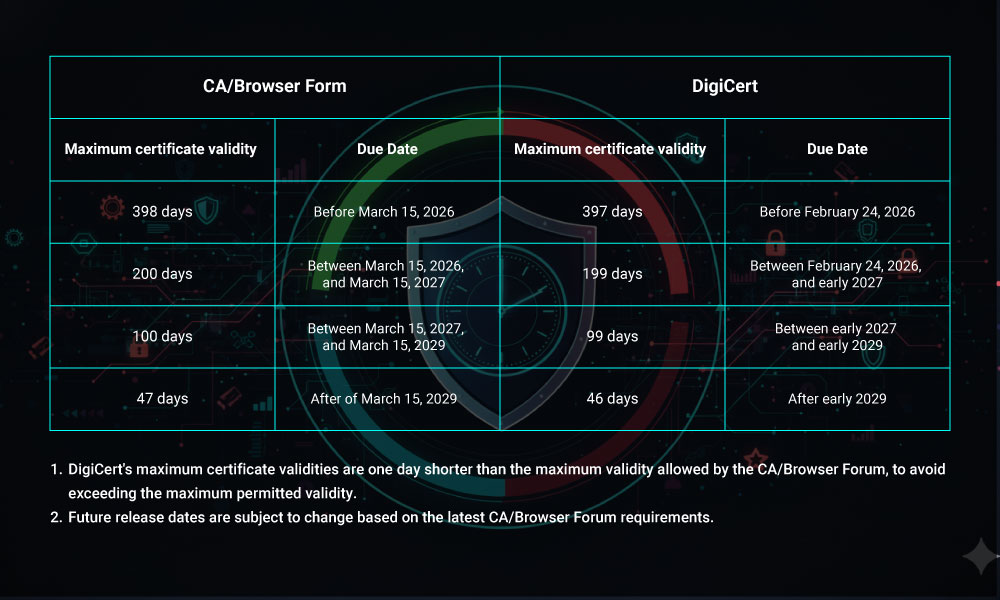
Background: Why Is TLS Certificate Validity Being Reduced?
Over the past decade, the maximum lifespan of public TLS certificates has been progressively shortened from multi-year certificates to 398 days, and now to 199 days.
The rationale behind shorter certificate validity periods includes:
- Reduced risk exposure if a certificate’s private key is compromised
- Faster response to mis-issuance or configuration errors
- Stronger overall trust in the public key infrastructure (PKI)
- Encouragement of automation and modern certificate management practices
The 199-day limit reflects continued alignment across the ecosystem, including certificate authorities, browser vendors, and security standards bodies.

What the 199-Day Validity Change Means for Enterprises
1. More Frequent Renewals
With a 199-day maximum validity, certificates will typically require renewal twice per year. Organizations that rely on manual or semi-manual processes may see:
- Increased administrative effort
- Higher coordination across teams
- Greater dependency on accurate inventory tracking
2. Increased Importance of Visibility
As renewal frequency increases, so does the importance of having a complete and accurate view of all certificates in use. Gaps in visibility can lead to:
- Unexpected certificate expirations
- Service disruptions
- Delays in incident response
3. Operational and Reliability Risks
TLS certificate expirations remain a common cause of:
- Website outages
- Application failures
- Broken API integrations
Shorter certificate lifespans increase the margin for error if renewals are missed or delayed.
4. Alignment With Automation Trends
The industry direction toward shorter-lived certificates reinforces the need for:
- Automated discovery of certificates
- Centralized lifecycle tracking
- Policy-driven renewal workflows
These capabilities help reduce human error and improve consistency across environments.
Key Dates and Scope
- Effective date: 24 February 2026
- Scope: All newly issued public TLS certificates from DigiCert
- Certificate types affected: DV, OV, and EV
Certificates issued before this date will remain valid until their original expiration, subject to existing rules.

Preparing for the Transition
- Reviewing existing certificate inventories and renewal processes
- Identifying dependencies on manual tracking methods
- Assessing current tooling for visibility and lifecycle management
- Aligning internal teams (security, IT, DevOps, operations) on ownership and responsibility
Summary
The move to 199-day TLS certificate validity represents another step in the industry’s evolution toward stronger, more resilient internet security. For enterprises, the change highlights the growing importance of structured Certificate Lifecycle Management, visibility, and operational discipline.
By understanding the implications early and preparing accordingly, organizations can adapt smoothly to the new validity model while maintaining reliability and security.
